World-class cybersecurity governance programs, tools, and guidance.
Decades of world-class cyber success in business-friendly SaaS tools, processes, and guidance, available as a fully managed vCISO service
Threat Profile
Pick your Battles
Fit-for-purpose cybersecurity begins with understanding your threat profile. You don't
need to be a cybersecurity expert for that.
Establish your Threat Profile
We've consolidated the universe of cyber threats into a handful of Threat Objectives
Align to Business Priorities
See your business description change in realtime as you adjust your Threat Profile
What-If Scenario Analysis
Preview the risk and policy changes driven by potential business changes
Risk and Incident Management
It's time to move beyond Sheets and Excel
You aren't alone. Even Fortune enterprises are managing their risk registers in a
spreadsheet - if they have one at all. Others are contorting expensive generic workflow
platforms to serve the purpose. What if seasoned long-term cybersecurity leaders built
Risk and Incident registers from the ground up to meet actual workflow and reporting
needs? Welcome to Adversarial.
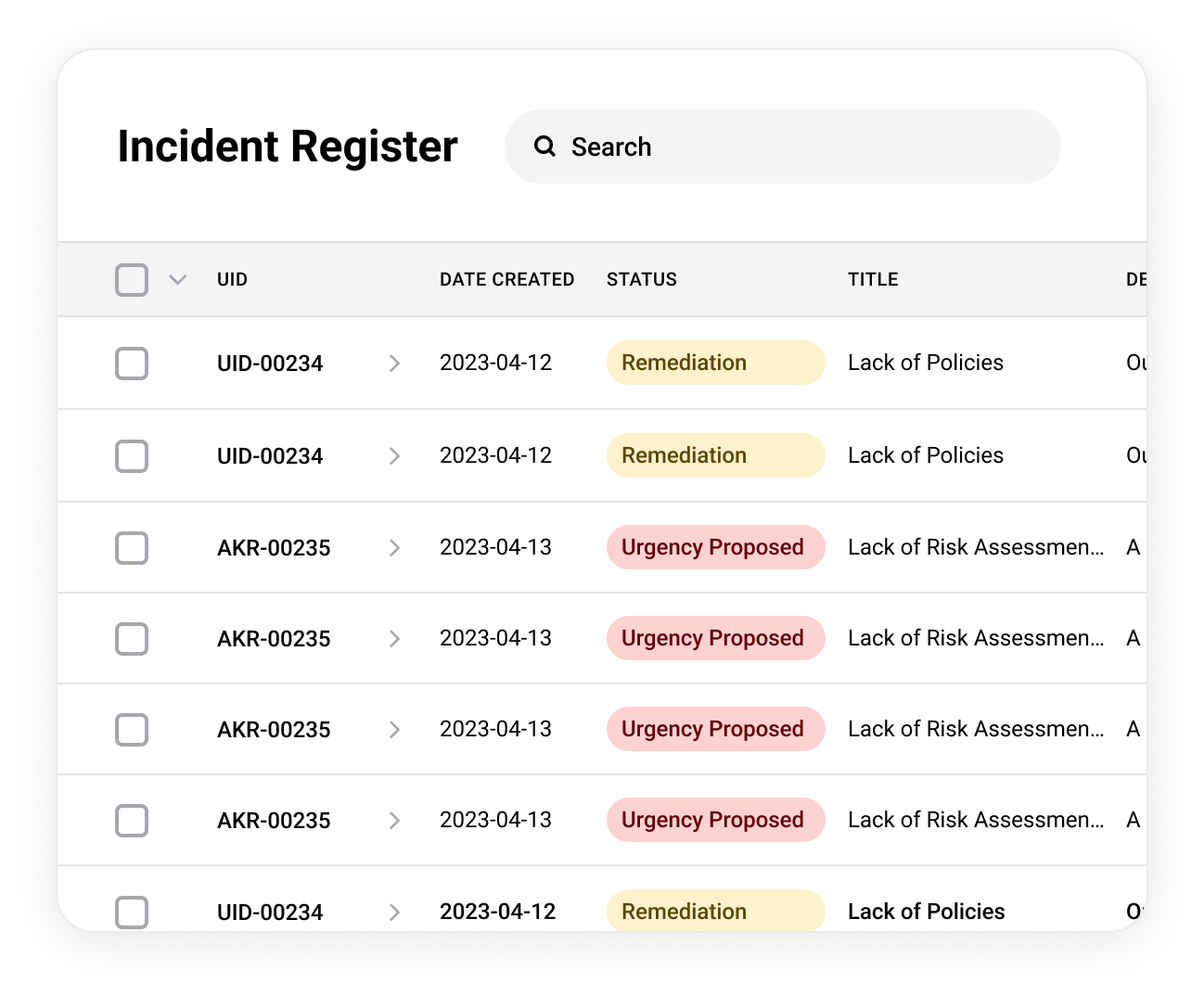
Intelligent Risk Register
Catalog and track your specific risks in a source-agnostic register, with a consistent
and clearly documented prioritization rubric.

Predictable Incident Management
Document potential incidents in a unified tool purpose-built to satisfy the latest
disclosure and escalation requirements.
Compliance
Stop Downloading Generic Policy Templates
One size doesn’t fit all. Boilerplate templates come back to bite you during audit when
you are penalized for not following draconian processes you never needed anyway. Our full
suite of policies, strategic documentation, procedures, and even committee charters are
dynamically tailored to your threat profile so every statement makes sense, is worth
implementing, and easily communicated.
You have to see it to believe it.
You have to see it to believe it.
Tailored policies
Strategic documentation & procedures
Committee charters